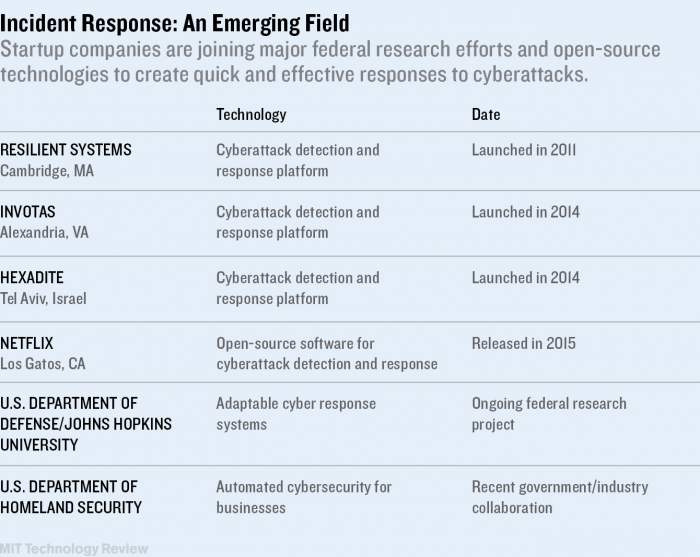
New Rapid Response Systems Blunt Cyberattacks
One reason breaches do so much damage is that they often remain undiscovered for months—an average of more than 200 days, according to research by the security firm Mandiant. Over time, a once-minor breach can become a catastrophe.
Sometimes the intrusion is hard to spot because the hacker has stolen legitimate credentials. Other times subtle hints of unusual network activity that might have revealed the attack are simply missed.
When such clues go unnoticed, it is often because large corporate security systems are so complex. It’s not unusual for a big company to use 70 or more different security monitoring tools made by many different companies and adopted over time—intrusion detectors, firewalls, Web-page monitors, spam filters, and many others. This common situation “is a huge problem,” says Jon Oltsik, cofounder of Enterprise Strategy Group, an IT research firm. “It depends on very, very smart people to figure out what each system is telling them and put together the total picture.”
One solution is for companies to replace whatever they’ve already installed with integrated systems from giant vendors like IBM, Cisco, and Raytheon. But that can be expensive and impractical for many.
So a growing crop of startups and research projects are beginning to offer approaches aimed at making it easier to tie existing systems together, while also making it possible to respond to attacks quickly and appropriately.
One early entrant, Resilient Systems, a startup in Cambridge, Massachusetts, captures data from a variety of sources and provides a single dashboard displaying all warnings. Then it presents a checklist of actions that must be taken, both to fix the problem and also to do things like notify the U.S. Federal Trade Commission or comply with state-by-state consumer notification laws.
Keep Reading
Most Popular
How scientists traced a mysterious covid case back to six toilets
When wastewater surveillance turns into a hunt for a single infected individual, the ethics get tricky.
The problem with plug-in hybrids? Their drivers.
Plug-in hybrids are often sold as a transition to EVs, but new data from Europe shows we’re still underestimating the emissions they produce.
What’s next for generative video
OpenAI's Sora has raised the bar for AI moviemaking. Here are four things to bear in mind as we wrap our heads around what's coming.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.