It’s simple and effective: getting someone to click a malicious link in an email and enter private information such as a password is the most important skill in many hackers’ toolkits. Phishing is the most common form of cyberattack and still growing.
And the reason it’s so effective, according to research being done at Google and the University of Florida, is that it takes advantage of how the human brain works—and, crucially, how people fail to detect deception, depending on factors like emotional intelligence, cognitive motivation, mood, hormones, and even the victim’s personality.
“We are all susceptible to phishing because phishing tricks the way our brain makes decisions,” Daniela Oliveira, an associate professor at the University of Florida, said on August 7 at the Black Hat cybersecurity conference in Las Vegas.
The problems begin with awareness: 45% of internet users don’t even know what phishing is, according to Oliveira and Google researcher Elie Bursztein.
Mood plays a role: people who are feeling happy and not stressed are less likely to detect deception in front of them. Cortisol, a stress hormone, increases vigilance and makes detecting a deception more likely. Serotonin and dopamine, hormones associated with positive feelings, can lead to risky and unpredictable behavior that make people more vulnerable.
Phishers can also be exceptionally good at crafting messages meant to persuade a person to click. Authority is among the most common and effective weapons—for instance, an email that claims to be from the company CEO, asking an employee to provide some information by clicking a link. Other tools include a gain/loss framing—for instance, a refund opportunity from Amazon.
Some of the most pointed phishing emails play on emotion. After the devastating and record-breaking California wildfires in 2018, Google saw an instant wave of emails asking for money to help victims. Emotional cues—for instance, promises to match donations for people left homeless—impaired the recipients’ ability to focus on the content and the clues that the email was a deception. By triggering this emotional response, the hackers got people to suspend their skepticism.
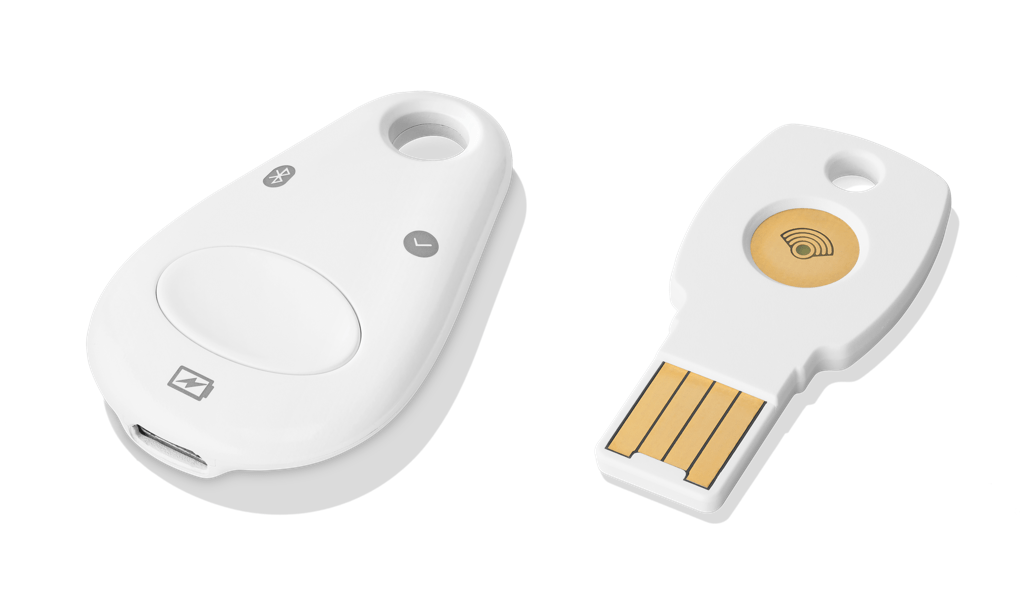
That doesn’t mean the only defense against phishing is to be a permanently stressed-out and cynical ball of anger. Healthier and more effective is to enable two-factor authentication for each of your important logins (email, online banking, social media, shopping sites, etc.). Here's a list of all the sites that support two-factor authentication.
When it’s enabled, the system asks you for something in addition to a password when you log in, such as a code sent to your phone via text message, a code from an authenticator app, or a physical security key on a USB stick (the most secure method of all, according to recent research). That way, if you’ve inadvertently given your password to a hacker in a phishing scam, they still won’t be able to log in to your account. Last year, Google said that fewer than 10% of its users had two-factor authentication enabled on their accounts.
Deep Dive
Computing
How ASML took over the chipmaking chessboard
MIT Technology Review sat down with outgoing CTO Martin van den Brink to talk about the company’s rise to dominance and the life and death of Moore’s Law.
Modernizing data with strategic purpose
Data strategies and modernization initiatives misaligned with the overall business strategy—or too narrowly focused on AI—leave substantial business value on the table.
Why it’s so hard for China’s chip industry to become self-sufficient
Chip companies from the US and China are developing new materials to reduce reliance on a Japanese monopoly. It won’t be easy.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.