First Quantum-Secured Blockchain Technology Tested in Moscow
Interest in cryptocurrencies is currently at fever pitch with banks, businesses, and governments racing to understand the technology and how they can exploit it. As a result, the cryptocurrency market has begun to rise exponentially, and last month reached an astonishing $90 billion in market capitalization. Whatever happens next, cryptocurrencies look certain to play an increasingly influential role in the global financial system.
But there is a problem on the horizon. The big challenge with digital cash is to ensure that everyone uses it honestly. And there seems to be a pretty good solution in the form of blockchain technology. This guarantees honesty using cryptographic techniques that are widely thought to be unbreakable, except by brute force attacks.
And therein lies the problem. Brute force attacks are difficult for classical computers but will be easy for the next generation of quantum computers. The vast number-crunching power of these devices mean that as soon as they are available, cryptocurrencies will be suddenly more vulnerable to attack.
So a way of securing blockchain technology against quantum attack would be hugely useful.
Enter Evgeny Kiktenko at the Russian Quantum Center in Moscow and a few pals who have designed, built, and tested a quantum blockchain system in which the security is guaranteed by quantum mechanics. They’ve built it using a standard quantum cryptography system of the kind that is already commercially available.
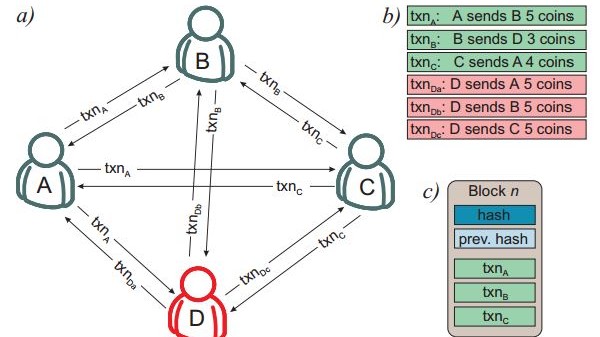
First some background. Blockchains record a list of transactions in a way that prevents dishonest use, such as tampering or double spending. They allow any computer to keep track of this list by compiling them into a block, which is then encrypted to form a number called a hash.
The encryption process is important. It is an algorithm that is easy to calculate but hard to do in reverse (like factorization). The hash value it produces is a unique property of the block, and any tampering with the records would be immediately obvious because this would change the hash.
New transactions are next gathered together into a new block and added to the existing hash value. This is then encrypted to create a new hash for the new block. This is added to the next list of transactions when they are encrypted, and so on. The result is a chain of blocks that each contain the hash values of all preceding blocks—hence the term blockchain.
All the computers that store these blocks regularly compare their hash values to ensure that they are all in agreement. Any computer that does not agree, discards the records that are causing the problem.
This approach is good but it is not perfect. One way to game this system is for a dishonest user to change the list of transactions in their favor, but in a way that leaves the hash unchanged. This can be done by brute force, in other words by changing a record, encrypting the result, and seeing whether the hash value is the same. And if not, trying again and again and again until it finds a hash that matches.
The security of blockchains is based on the belief that ordinary computers can only perform this kind of brute force attack over time scales that are entirely impractical, such as the age of the universe. By contrast, quantum computers are much faster and consequently pose a much greater threat.
Kiktenko and co have a solution that prevents quantum attacks of this kind. Their blockchain technology is subtly different. A transaction between two individuals contains the information about the sender, the receiver, the time of creation, the amount to be transferred, and a list of reference transactions that justifies that the sender has enough funds for the operation.
This transaction is then sent to all the computers in the currency network who store it until some pre-agreed time—10 minutes, say—when the transactions are gathered together into a block.
The next stage uses an algorithm that allows all parties to agree that the list of transactions is honest. This is based on proof from the 1980s in which everybody first shares their information with all other computers. Next, they communicate the information they received from the other parties in the network allowing everyone to see who said what. The parties then share this information in yet another round and so on until they agree that all computers have the same information.
The proof is that it is always possible to reach a consensus in fewer rounds than there are parties, provided that at least two-thirds of the parties are honest.
But in such a system how can Alice be sure she is receiving information from Bob and vice versa? Without this certainty, it is easy for a malicious user to game the system by pretending to be lots of different users.
This is where quantum mechanics comes in. Alice and Bob can verify each other’s identities using a technique called quantum key distribution. This sends information using quantum particles such as photons, which cannot be copied by an eavesdropper without destroying them. In this way, Alice and Bob can be sure of each other’s identity.
So the bedrock of Kiktenko and co’s system is a quantum identification system in which each party can verify the identity of any other in a way that is guaranteed by the laws of physics. This quantum signature is attached to every transactions making it impossible to tamper with.
Kiktenko and co say they have built just such a system using commercially available quantum cryptography system from the Swiss company ID Quantique. “We have developed a blockchain protocol with information-theoretically secure authentication based on a network in which each pair of nodes is connected by a quantum key distribution link,” they say.
And they’ve tested it in a network of four users, one of which is attempting to game the system by double spending. “This protocol eliminates [the] double-spending transaction after the second communication round and permits the formation of a block containing legitimate transactions only,” say Kiktenko and co.
That’s an interesting proof-of-principle experiment that shows how quantum techniques can be used to secure blockchain technologies.
But it is not perfect. In particular, it assumes that fewer than one third of the parties are dishonest. If more than a third of users agree to game the system, it becomes trivial to do so.
There are also significant technology hurdles in making this system work on a larger scale. Not least of these is the creation of a quantum Internet to allow these kinds of transaction to take place over long distances. That’s a challenge that should be overcome given that it is currently being tackled by researchers all over the world.
The threat from quantum computers is certainly real—and not just for blockchain technology. Any information that is currently stored using conventional cryptography will become unsecure as soon as the first powerful-enough quantum computer is switched on.
With the sudden rush to use cryptocurrencies, it would clearly be useful to future-proof the technology against this quantum threat.
Ref: arxiv.org/abs/1705.09258: Quantum-Secured Blockchain
Deep Dive
Computing
How ASML took over the chipmaking chessboard
MIT Technology Review sat down with outgoing CTO Martin van den Brink to talk about the company’s rise to dominance and the life and death of Moore’s Law.
Why it’s so hard for China’s chip industry to become self-sufficient
Chip companies from the US and China are developing new materials to reduce reliance on a Japanese monopoly. It won’t be easy.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.