How Smart Is a Smart Card?
Waving a Smart card in front of a radio frequency identification (RFID) reader can provide access to buildings, pay for subway rides, and even initiate credit-card transactions. With more than a billion units sold, the NXP Mifare Classic RFID tag is the most commonly used smart-card chip; it can be found in the London subway system’s Oyster card, Australia’s SmartRider, and the Boston subway’s Charlie Card. Security researcher Karsten Nohl, who recently got his PhD in computer science from the University of Virginia, and ”Starbug,” a member of a Berlin hacker group called the Chaos Computer Club, hacked into a Mifare Classic’s hardware to gain insight into its cryptographic algorithms. After analyzing the chip, Nohl questioned its security in a series of presentations at recent conferences, including Black Hat in Las Vegas.
An Acetone Bath
Melting a smart card with acetone reveals an RFID chip within (visible in the lower right at the end of the video). The process takes about a half hour. After extracting the chip, a hacker can process it further to analyze its construction and programming.
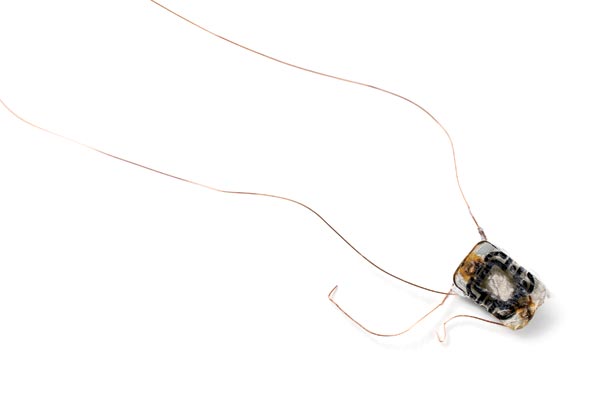
RFID Chip
Nohl and Starbug used acetone to peel the plastic off the card’s millimeter-square chip. Once they isolated the chip, they embedded it in a block of plastic and sanded it down layer by layer to examine its construction. Nohl compares this to looking at the structure of a building floor by floor.
Layers
The chip has multiple layers that perform different functions, which the researchers had to tease apart in order to identify and understand its algorithms. Since the sanding technique didn’t work perfectly, it produced a series of partial images. Nohl and Starbug borrowed techniques from panoramic photography to create a clear composite image of each layer. They identified six in all: a cover layer, three interconnection layers, a logic layer, and a transistor layer.
Images Credit: Christopher Harting; Interactive Credit: Alastair Halliday
Logic and Transistor Layers
A close look at these layers reveals about 10,000 groups of transistors, which execute the algorithms that run the chip. Nohl and Starbug’s analysis revealed that each group performs one of 70 logic functions, and that the groups are repeated in different patterns.


Interconnection Layers
Several layers of metal between the protective cover layer and the logic layer provide the connections between the different logic functions. Wires running through them control the flow of current through the groups of transistors.

Logic Gates
The groups of transistors that perform the chip’s logical operations are known as logic gates. By analyzing the pattern of logic gates on the chip, the researchers determined which circuits performed which functions; for example, a string of one-bit memory cells known as flip-flops pointed to the part of the chip responsible for cryptography. The researchers made a map of the logic gates and the connections between them, which allowed them to uncover the chip’s cryptographic algorithm and determine that it was weak. Nohl says that RFID security could be improved by the use of stronger, peer-reviewed algorithms, along with measures to obscure or tamper-proof the circuit itself.

Keep Reading
Most Popular
Large language models can do jaw-dropping things. But nobody knows exactly why.
And that's a problem. Figuring it out is one of the biggest scientific puzzles of our time and a crucial step towards controlling more powerful future models.
How scientists traced a mysterious covid case back to six toilets
When wastewater surveillance turns into a hunt for a single infected individual, the ethics get tricky.
The problem with plug-in hybrids? Their drivers.
Plug-in hybrids are often sold as a transition to EVs, but new data from Europe shows we’re still underestimating the emissions they produce.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.