Sponsored
Facing tomorrow’s quantum hackers today
Organizations need to strengthen their cybersecurity now before quantum computing becomes powerful enough to break today’s encryptions.
In collaboration withAbu Dhabi’s Technology Innovation Institute
When it comes to computing ability, the general rule of thumb is more is better. Quantum computers promise to feed this hunger. Their immense processing power comes from their ability to store and handle significantly larger volumes of data than classical bit-driven computers. The result—a future quantum computer could, in theory, take minutes to solve problems that take classical computers tens of thousands of years.
Facing tomorrow’s quantum hackers today
The possibilities of such computing power are enormous. Sifting through libraries of molecular combinations to accelerate drug discoveries, tightening logistics planning, boosting computational chemistry, fine-tuning weather forecasting accuracy, and strengthening financial modeling are a few of the applications waiting in the wings.
Quantum computing could create a “value of $450 billion to $850 billion in the next 15 to 30 years,” according to estimates from a 2021 report from Boston Consulting Group. Governments and private companies around the world recognize this potential and are working to develop their own quantum strategies and research initiatives.
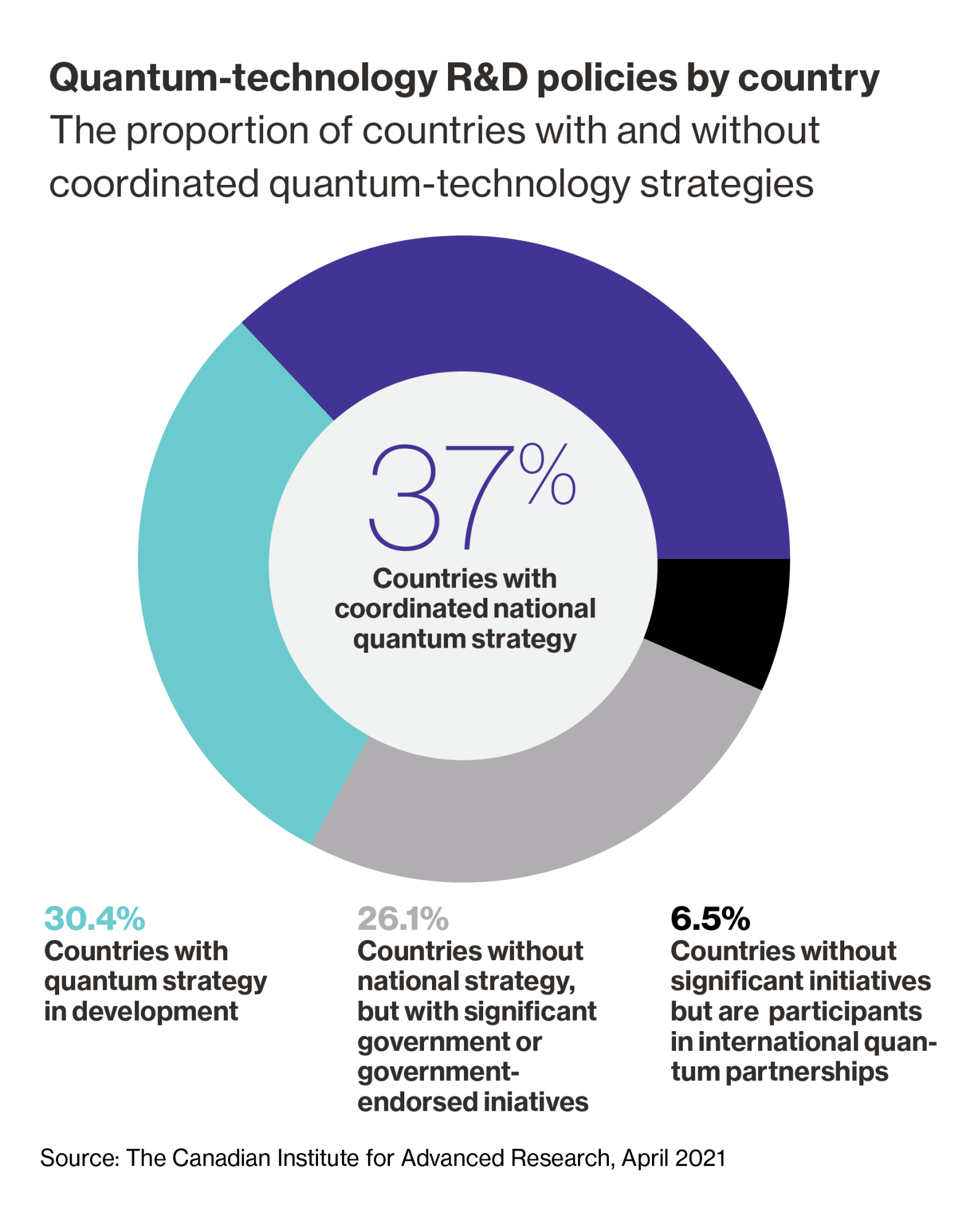
Bracing for the power of quantum
However, as quantum technology continues to advance, one dark cloud lurks on the horizon. Hackers could one day use this processing power to break public-key cryptography systems, which form the basis for today’s secure interactions over the Internet, as well as other systems such as public-key infrastructure, code-signing systems, secure email, and key-management systems. Experts warn this is a major threat to modern digital security that needs to be tackled now. “It will completely break these crypto systems,” says Dustin Moody, a mathematician at US-based National Institute of Standards and Technology (NIST).
Although a full-scale quantum computer has yet to become reality, the danger is imminent. Duncan Jones, head of cybersecurity at a Cambridge- and Colorado-based quantum computing company, Quantinuum, says he’s concerned about a particular problem. “If I send you some encrypted data today and somebody records that, they can break into that later on,” says Duncan. “They don't need a quantum computer today to break into it. They can just patiently sit on that data and they can then decrypt in the future.”

Post-quantum cryptography is emerging as an efficient and effective solution to defend against such quantum attacks. This solution is a set of new cryptographic algorithms, in particular public-key algorithms, that can be implemented using today’s classical computers.
There is growing urgency for enterprises of all sizes and across all industries, as well as public institutions and other organizations, to make their systems crypto-agile and adopt such quantum-resistant algorithms in their security frameworks. Companies and organizations cannot afford to wait and see how the quantum-computing landscape evolves. “The cost will blow up if it is adopted after quantum computers are established,” says Jung Hee Cheon, professor of mathematics at Seoul National University in South Korea. Given the high stakes, a proactive, rather than reactive, stance toward such threats is crucial.
This content was produced by Insights, the custom content arm of MIT Technology Review. It was not written by MIT Technology Review’s editorial staff.
Deep Dive
Computing
How ASML took over the chipmaking chessboard
MIT Technology Review sat down with outgoing CTO Martin van den Brink to talk about the company’s rise to dominance and the life and death of Moore’s Law.
Why it’s so hard for China’s chip industry to become self-sufficient
Chip companies from the US and China are developing new materials to reduce reliance on a Japanese monopoly. It won’t be easy.
Modernizing data with strategic purpose
Data strategies and modernization initiatives misaligned with the overall business strategy—or too narrowly focused on AI—leave substantial business value on the table.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.