The 20 Most Infamous Cyberattacks of the 21st Century (Part II)
Tavish Vaidya at Georgetown University in Washington, D.C., has been studying trends in cyberattacks that have occurred since 2000. His conclusion is that they are on the increase and that precautions must be taken to secure important data as a matter of urgency.
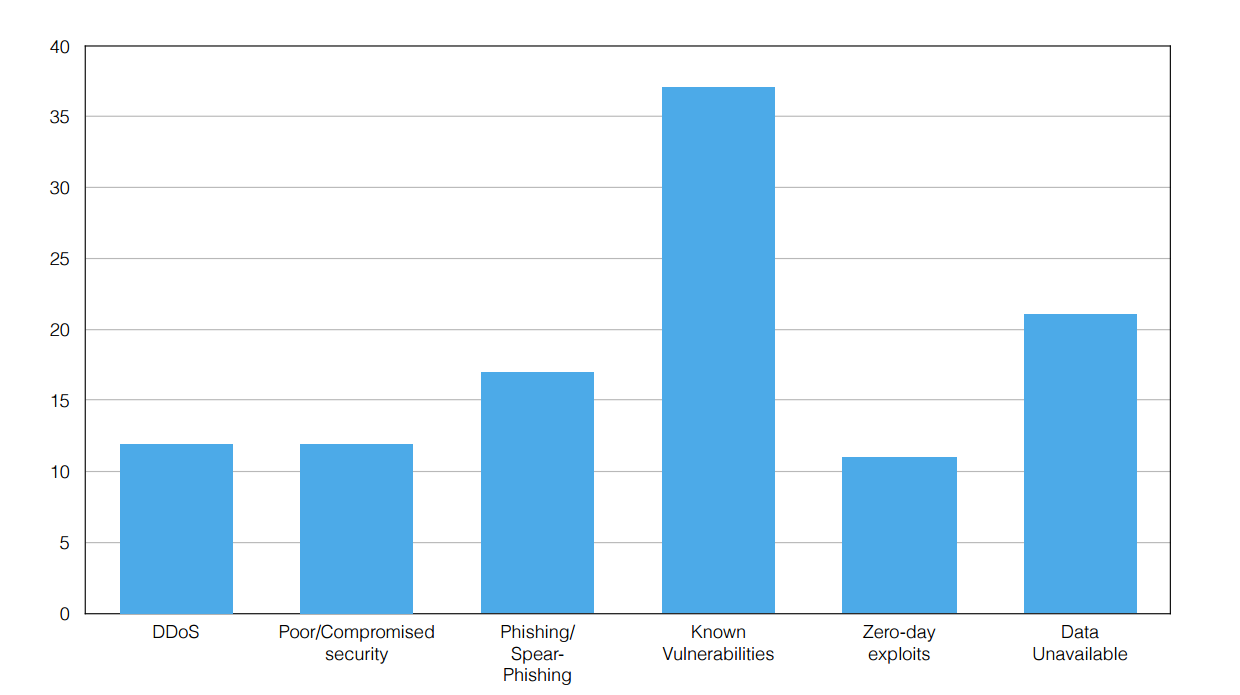
Worryingly, he says the same attacks are appearing over and over again. “Attacks exploiting known vulnerabilities are not subsiding,” he says. “This shows that valuable lessons are not being learned from past experiences.”
Here is the second part of a list of the most egregious examples…
10. February 2009: Newspapers report that the Conficker worm infection has grounded French fighter planes and also hit computers on board Royal Navy warships and submarines.
9. March 2011: the security company RSA announces that hackers have targeted its employees with phishing e-mails carrying malware that allow remote control of the company’s computers. This allowed hackers to gain access to the RSA network and compromise the company’s entire system of SecureID tokens that its customers use to protect their networks. The attack cost RSA some $66 million dollars to replace customers’ SecureID tokens.
8. April 2011: sensitive information is stolen from the American defense contractor L-3 Communications using stolen SecureID tokens thought to have come from the RSA breach. Lockheed Martin is also attacked in the same way, although not successfully.
7. August 2011: Operation Shady RAT is exposed as having attacked more than 70 corporations and government organizations around the world, including defense contractors and the United Nations. The attacks began in 2006 and in 2008 targeted various athletics governing bodies before the Summer Olympic in Beijing. The attack is thought to have originated in China.
6. January 2003: The Slammer worm disables safety monitoring systems at Ohio’s Davis-Besse nuclear power plant for five hours. The system had an analogue back up which was unaffected by the attack and, in any case, the power plant had been off line for several years for repairs. Nevertheless, the incident demonstrates how vulnerable critical infrastructure can be.
5. January 2010: Google announces that it has been attacked via a vulnerability in Adobe Reader in an action dubbed Operation Aurora by security experts. The same attack also hit more than 30 other companies including Yahoo, Symantec Adobe, and Northrop Grumman.
4. October 2010 U.S. banks lose over $12 million in an attack that used a trojan called Zeus to record keystrokes to steal bank account details. Around 100 people are charged as suspects.
3. December 2013: Chinese hackers are reported to have used phishing techniques to inject malware into the computers of European G20 members attending a G20 meeting in St Petersburg. The attackers reportedly accessed details of the U.S.’s proposed military involvement in Syria.
2. April 2011. Sony’s Playstation network is hacked leading to the theft of personal and credit card details associated with up to 77 million users, possibly the largest identity theft in history. The hack costs Sony $171 million in legal costs, a “welcome back” campaign and various other costs.
1. June 2010: computer security researches discover a computer worm called Stuxnet designed to attack programmable logic controllers in industrial machinery. The worm is thought to have been created by the U.S. and Israeli cyberwarfare teams to attack Iran’s Natanz uranium enrichment plant. The worm seems designed to alter the speed of uranium enrichment centrifuges in a way that generates vibrations strong enough to destroy them. Other reports suggest that Stuxnet damaged around 1,000 centrifuges, reducing the number in operation in Iran from 4,700 to 3,900.
Ref: arxiv.org/abs/1507.06673 : 2001-2013: Survey and Analysis of Major Cyberattacks
Keep Reading
Most Popular
Large language models can do jaw-dropping things. But nobody knows exactly why.
And that's a problem. Figuring it out is one of the biggest scientific puzzles of our time and a crucial step towards controlling more powerful future models.
The problem with plug-in hybrids? Their drivers.
Plug-in hybrids are often sold as a transition to EVs, but new data from Europe shows we’re still underestimating the emissions they produce.
How scientists traced a mysterious covid case back to six toilets
When wastewater surveillance turns into a hunt for a single infected individual, the ethics get tricky.
Google DeepMind’s new generative model makes Super Mario–like games from scratch
Genie learns how to control games by watching hours and hours of video. It could help train next-gen robots too.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.