The Truth About Smartphone Apps That Secretly Connect to User Tracking and Ad Sites
There are essentially two starkly different environments in which to download apps. The first is Apple’s app store, which carefully vets apps before allowing only those deemed fit to appear. The second is the Google Play store, which is more open because Google exercises a lighter touch in vetting apps, only excluding those that are obviously malicious.
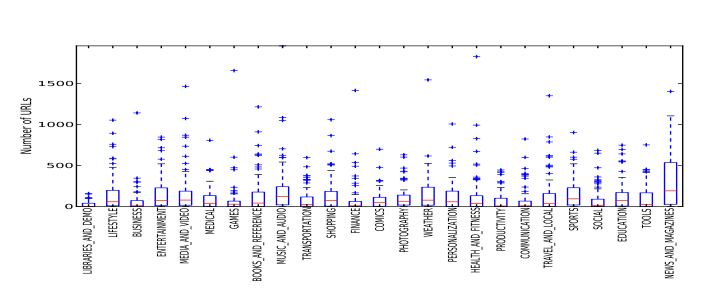
But because Google Play is more open, the apps it offers span a much wider quality range. Many connect to ad-related sites and tracking sites while some connect to much more dubious sites that are associated with malware.
But here’s the problem—this activity often takes place without the owner being aware of what is going on. That’s something that most smartphone users would be appalled to discover—if only they were able to.
Today, Luigi Vigneri and pals from Eurecom in France have a solution. These guys have come up with an automated way to check the apps in Google Play and monitor the sites they connect to. And their results reveal the extraordinary scale of secret connections that many apps make without their owners being any the wiser.
Vigneri and co began by downloading over 2,000 free apps from all 25 categories on the Google Play store. They then launched each app on a Samsung Galaxy SIII running Android version 4.1.2 that was set up to channel all traffic through the team’s server. This recorded all the urls that each app attempted to contact.
Next they compared the urls against a list of known ad-related sites from a database called EasyList and a database of user tracking sites called EasyPrivacy, both compiled for the open source AdBlock Plus project. Finally, they counted the number of matches on each list for every app
The results make for interesting reading. In total, the apps connect to a mind-boggling 250,000 different urls across almost 2,000 top level domains. And while most attempt to connect to just a handful of ad and tracking sites, some are much more prolific.
Vigneri and co give as an example “Music Volume Eq,” an app designed to control volume, a task that does not require a connection to any external urls. And yet the app makes many connections. “We find the app Music Volume EQ connects to almost 2,000 distinct URLs,” they say.
And it is not alone in its excesses. The team say about 10 percent of the apps they tested connect to more than 500 different urls. And nine out of 10 of the most frequently contact ad-related domains are run by Google.
The user tracking sites that apps connect to are less pervasive. More than 70 percent of apps do not connect to any user tracking sites. But those that do can be extravagant, some connecting to more than 800 user tracking sites. What’s more many of these are created by organizations that Google has designated with “top developer status.” The worst offender is an app called Eurosport Player which connects to 810 different user tracking sites.
A small proportion of the apps even seem designed to connect to suspicious sites connected with malware.
Most users of these apps will have little, if any, knowledge of this kind of behavior. So Vigneri and co have developed their own app that monitors the behavior of others on a user’s smartphone and reveals exactly which external sites these apps are attempting to connect to.
They call their new app NoSuchApp or NSA for short “in honor of a similarly acronymed monitoring agency.”
That should give Android users confidence in the apps they use. “With this application, our goal is to provide a mechanism for end users to be aware of the network activity of their installed Android applications,” say Vigneri and co.
The team plan to make the app publicly available on Google Play in the near future.
Ref: arxiv.org/abs/1504.06093 : Taming the Android AppStore: Lightweight Characterization of Android Applications
Keep Reading
Most Popular
Large language models can do jaw-dropping things. But nobody knows exactly why.
And that's a problem. Figuring it out is one of the biggest scientific puzzles of our time and a crucial step towards controlling more powerful future models.
The problem with plug-in hybrids? Their drivers.
Plug-in hybrids are often sold as a transition to EVs, but new data from Europe shows we’re still underestimating the emissions they produce.
How scientists traced a mysterious covid case back to six toilets
When wastewater surveillance turns into a hunt for a single infected individual, the ethics get tricky.
Google DeepMind’s new generative model makes Super Mario–like games from scratch
Genie learns how to control games by watching hours and hours of video. It could help train next-gen robots too.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.