Windows XP Is Still a Favorite Among Hackers
It’s been 13 years since Windows XP came out and more than six months since Microsoft stopped issuing security updates for the operating system, but the software remains in wide use—and a new analysis shows it’s a huge resource for cybercriminals.
Researchers at the security firm Proofpoint recently gained access to a server that a group of Russian-speaking hackers was using to control a botnet consisting of 500,000 hacked PCs, most of which are located in the United States.
The PCs were infected by a piece of malware called Qbot that not only steals online banking information but also adds the infected machine to a botnet network that is leased to other criminals. Wayne Huang, one of the authors of Proofpoint’s report, says the network could be used to transfer stolen data or to infiltrate organizations.
Huang and his colleagues note that over half of the computers in the botnet were running Windows XP. While it is common for computers running XP to make up large portions of a botnet, Huang says he and his colleagues were surprised to see so many in this case, since it’s been half a year since Microsoft stopped supporting the OS.
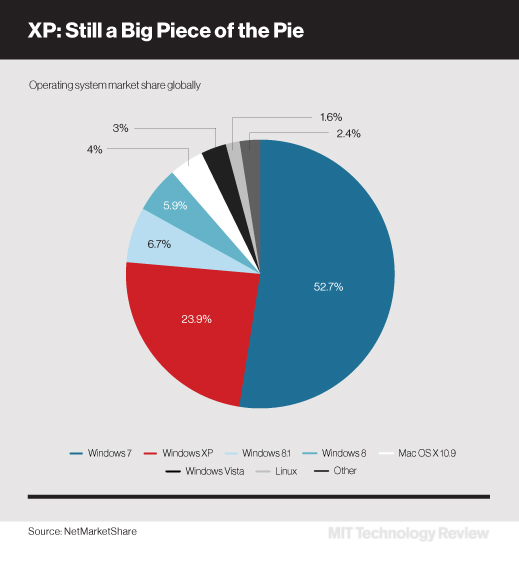
Estimates by NetMarketShare, a market research firm, suggest that 24 percent of more than 1.5 billion total PCs worldwide are still running XP. Back in April, when Microsoft discontinued its support of XP, the security firm Qualys found that the operating system was still widely used in the finance, transport, and retail industries.
Relatively few new XP vulnerabilities have been documented this year compared to each of the previous years since the product’s launch, according to the MITRE Corporation, which maintains a record of common vulnerabilities. In the case of the botnet that Proofpoint analyzed, its creators appear to be using exploits that are a year or two old, says Huang.
Nonetheless, it makes sense for cybercriminals to continue exploiting XP, says Carl Leonard, senior manager of security research for Websense. In fact, he says, some hackers may be stockpiling XP vulnerabilities, waiting for the right target—many millions of XP machines are in China and other parts of the world where pirated editions are prevalent.
“You are at risk if you still run XP,” says Leonard. “The risk will only increase going forward.”
Keep Reading
Most Popular
Large language models can do jaw-dropping things. But nobody knows exactly why.
And that's a problem. Figuring it out is one of the biggest scientific puzzles of our time and a crucial step towards controlling more powerful future models.
The problem with plug-in hybrids? Their drivers.
Plug-in hybrids are often sold as a transition to EVs, but new data from Europe shows we’re still underestimating the emissions they produce.
Google DeepMind’s new generative model makes Super Mario–like games from scratch
Genie learns how to control games by watching hours and hours of video. It could help train next-gen robots too.
How scientists traced a mysterious covid case back to six toilets
When wastewater surveillance turns into a hunt for a single infected individual, the ethics get tricky.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.