One-Time Pad Reinvented to Make Electronic Copying Impossible
One-time pads are the holy grail of cryptography—they are impossible to crack, even in principle.
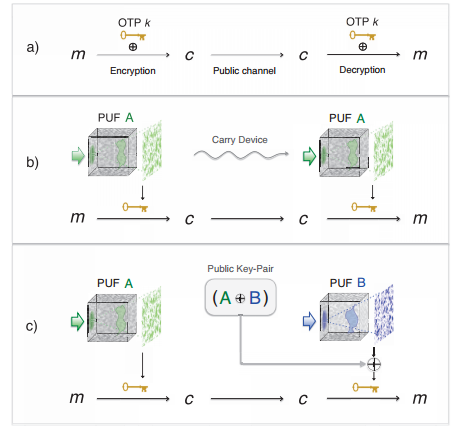
They work by adding a set of random digits to a message thereby creating a ciphertext that looks random to any eavesdropper. The receiver decodes the message by taking away the same set of random digits to reveal the original message.
The security of this process depends on two factors. The first is the randomness of the digits that make up the one-time pad. If this key is truly random, it offers nothing the eavesdropper can use to break the code. Although there are some potential pitfalls, random digits are reasonably straightforward to generate these days.
The second factor is the ability to keep this key secret so that only the transmitter and receiver have access to it. That’s much more difficult to ensure.
Digital communication in the form of 0s and 1s makes copying trivial. Whenever a set of random digits is stored in an electronic memory, there is always a small but finite chance that it can be quickly copied and stolen.
Today, Roarke Horstmeyer at the California Institute of Technology in Pasadena and a few buddies say they’ve solved this problem. Their solution is based on a special kind of one-time pad that generates a random key through the complexity of its physical structure.
Instead of creating and storing the one-time pad as a random sequence of 0s and 1s, Horstmeyer and co generate a random signal by passing light through a slab of diffusing glass that scatters it randomly.
The security of the system depends on the physical complexity of the glass. Horstmeyer and co say that that this complexity means there is no way for an eavesdropper, “Eve,” to copy the glass without anyone noticing.
That cuts out the need to store the key electronically and entirely removes this vulnerability to copying. “We describe an encrypted communication principle that can form a perfectly secure link between two parties without electronically saving either of their keys,” they say
And even if Eve steals the glass, they estimate that it would take her at least 24 hours to extract any relevant information about its structure.
This extraction can only be done by passing light through the glass at a rate that is limited by the amount of heat this creates (since any heating changes the microstructure of the material). And the time this takes should give the owners enough time to realise what has happened and take the necessary mitigating actions.
The protocol for sending secret messages between “Alice” and “Bob,” say, is straightforward. To start off, both Alice and Bob must have their own slabs of diffusing glass and must physically meet to create a key for encoding a message later.
They create this by sending the same random pattern of light through their diffusing slabs and then adding the results to create a combined key.
They then publish this combined key and the pattern used to create it.
To send a message, Alice sends the pattern through her slab to generate her half of the key and then adds it to her message. She can now send this without fear that Eve can decode it.
It’s important to remember that Alice’s random key is a component of the publicly available one. But Eve cannot use the publicly available key to work out what Alice’s key is.
Bob has to go through a slightly different set of steps to decode this cyphertext. First, having received the cyphertext, he adds it to the publicly available combined key.
Next, he re-creates his own component of the publicly available key by sending the publicly available pattern through his slab. He then adds this to the result of the previous step to reveal the message.
As long as both diffusing slabs are physically held by Alice and Bob, the cyphertext cannot be decoded by Eve.
Of course, this process can be used only once. But Alice and Bob can generate a huge volume of combined keys by passing different random patterns through their slabs when they meet.
Horstmeyer and co have tested their idea using a spatial light modulator to create random patterns that they then pass through opal diffusing glass to generate about 10 gigabits of randomness. They then used this for sending perfectly secure messages, thereby demonstrating the utility of the technique.
Nevertheless, improvements should be possible, they say. For example, the team says that the system generates a small amount of noise caused by the natural drift of scatterers in the glass over time. But that’s something that should be possible to fix with error-correcting codes.
And it ought to be possible to generate a terabit of randomness from a single cubic millimetre of diffusing glass with higher-resolution equipment.
And even thought this can only be used once, the slabs can be easily reset by heating the glass to change its microstructure at which point Alice and Bob must meet again to create a new set of combined keys.
That looks to be a significant improvement over any kind of cryptography that stores keys electronically and is therefore vulnerable to an electronic attack that can copy digital information perfectly.
“Compared with a large, electronically saved one-time pad, [the new system’s] key is extremely challenging to copy or model and can easily scale to provide terabits of repeatable randomness within a small volume,” say Horstmeyer and co.
They have high hopes for this approach: “We hope the convenient properties of optical scattering can solve enough of the one-time pad’s practical shortcomings to rejuvenate interest in its unbreakable security, even in the presence of infinite computing resources.”
What they mean is that this system should be secure even to attack with future quantum computers.
That’s not something that can be said about the codes commonly used to protect messages today. With quantum computers now beginning to perform some serious calculations, anybody still using these codes must be losing a significant amount of sleep.
Ref: arxiv.org/abs/1305.3886: Physical Key-Protected One-Time Pad
Keep Reading
Most Popular
Large language models can do jaw-dropping things. But nobody knows exactly why.
And that's a problem. Figuring it out is one of the biggest scientific puzzles of our time and a crucial step towards controlling more powerful future models.
The problem with plug-in hybrids? Their drivers.
Plug-in hybrids are often sold as a transition to EVs, but new data from Europe shows we’re still underestimating the emissions they produce.
Google DeepMind’s new generative model makes Super Mario–like games from scratch
Genie learns how to control games by watching hours and hours of video. It could help train next-gen robots too.
How scientists traced a mysterious covid case back to six toilets
When wastewater surveillance turns into a hunt for a single infected individual, the ethics get tricky.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.