Breaches and Security, By the Numbers
How is corporate data being stolen? Attacks often employ multiple methods—but remotely hacking a computer isn’t always one of them. Sometimes employees are involved, and some attackers physically break in. The numbers in the chart below total more than 100 percent because more than one method can be used in an attack.
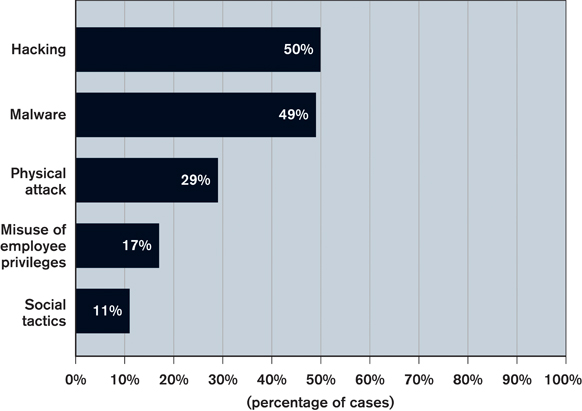
Source: Verizon’s 2011 Data Breach Investigations Report, which analyzed 761 breaches
Given all the ways data breaches can occur, companies need to employ multiple methods of defense. This chart shows the main steps they are taking. Nearly half, for example, are removing data from the network rather than risk having it stolen. Companies often pursue several protective strategies, which is why the percentages total more than 100.
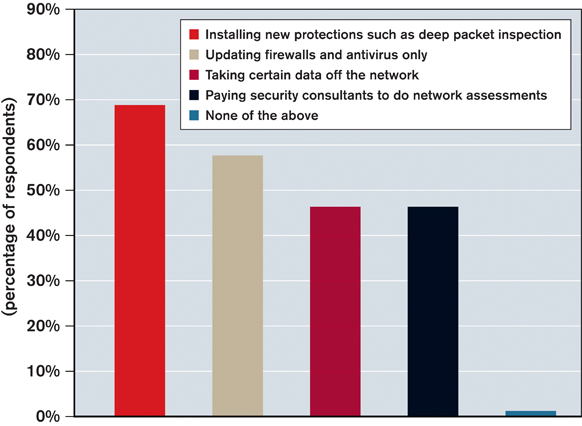
Source: Survey of more than 1,000 senior IT executives worldwide for Underground Economies, a 2011 report by McAfee and Science Applications International Corporation (SAIC)
As this year’s high-profile data breaches have shown, many organizations’ security measures are not proving resilient enough. This chart shows the 12 most common ways for companies to learn they have been breached.

Source: Verizon’s 2011 Data Breach Investigations Report.
Failing to turn the tide against data breaches is proving costlier each year. This chart shows the percentage of IT operating budgets that companies have been devoting to security.
Source: Forrester Research surveys in 2007, 2008, 2009, and 2010
Keep Reading
Most Popular
Large language models can do jaw-dropping things. But nobody knows exactly why.
And that's a problem. Figuring it out is one of the biggest scientific puzzles of our time and a crucial step towards controlling more powerful future models.
How scientists traced a mysterious covid case back to six toilets
When wastewater surveillance turns into a hunt for a single infected individual, the ethics get tricky.
The problem with plug-in hybrids? Their drivers.
Plug-in hybrids are often sold as a transition to EVs, but new data from Europe shows we’re still underestimating the emissions they produce.
Google DeepMind’s new generative model makes Super Mario–like games from scratch
Genie learns how to control games by watching hours and hours of video. It could help train next-gen robots too.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.