Out-of-Work Chinese Government Hackers May Be Behind Sophisticated Ransomware Attacks
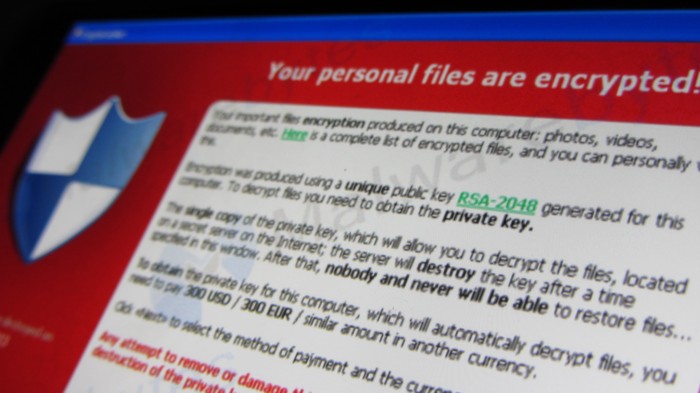
Malicious software that holds data hostage using encryption has already proved devastatingly effective and very lucrative for criminals. Now some of the Internet’s most sophisticated criminals are getting in on the act, targeting corporations as a quick path to profit.
Reuters reports that four leading security firms have seen ransomware used against U.S. companies by people who appear to be associated with hacking groups that work at the behest of China’s government. Such groups usually target corporate secrets in sophisticated operations that experts say are state-sponsored economic espionage.
Victims of this new high-end ransomware include transportation and technology companies, according to Reuters. Their report doesn’t say how big a ransom the attackers asked for, but groups with enough skill might be able to hold very valuable data hostage and demand large payouts.
By contrast, ransomware is usually spread as widely as possible by criminals who demand modest sums for the safe return of data, typically around $500, because they want to collect from individuals as well as companies.
Why hackers who usually work for a superpower might start using a small-time criminal tactic is unclear. One reason is that deploying ransomware might be an easy way to extract some extra money once a conventional espionage job is over.
A more intriguing possibility is that these might be lean times for China’s industrial espionage hackers. Late last year President Obama and his Chinese counterpart Xi Jinping agreed not to support theft of intellectual property, and to assist each other in investigating cases that did occur. The deal was seen as a breakthrough after years of U.S. complaints about computer incursions from China.
That agreement may have caused China to cut back on its sponsorship of hackers, driving them to find alternative forms of income, the security companies reporting the new malware campaigns told Reuters. If that theory is correct, companies might expect to see less of their data headed to China, but more of it locked up by malware with a ransom note attached.
Either way, we can expect ransomware to become more common. The FBI’s Internet Crime Complaint Center said on March 10 that it was notified of 2,453 ransomware infections by victims in 2015, who collectively paid $24.1 million to get their data back. The true figure for the U.S. is likely to be much higher, and the FBI expects the problem to grow.
(Read more: Reuters, Wall Street Journal, “Holding Data Hostage: The Perfect Internet Crime?” “Waiting for a Drop in Corporate Hacks After U.S.-China Deal,” “Hospital Forced Back to Pre-Computer Era Shows the Power of Ransomware”)
Keep Reading
Most Popular
Large language models can do jaw-dropping things. But nobody knows exactly why.
And that's a problem. Figuring it out is one of the biggest scientific puzzles of our time and a crucial step towards controlling more powerful future models.
The problem with plug-in hybrids? Their drivers.
Plug-in hybrids are often sold as a transition to EVs, but new data from Europe shows we’re still underestimating the emissions they produce.
Google DeepMind’s new generative model makes Super Mario–like games from scratch
Genie learns how to control games by watching hours and hours of video. It could help train next-gen robots too.
How scientists traced a mysterious covid case back to six toilets
When wastewater surveillance turns into a hunt for a single infected individual, the ethics get tricky.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.