Security Flaw Shows Tor Anonymity Network Dominated by Botnet Command and Control Traffic
The Tor network is an online service that allows users to surf the web anonymously. Its main benefit is to reduce the chances of network surveillance discovering a user’s location or web usage. For that reason it is championed as an important tool for promoting free speech and protecting personal privacy, especially for people under authoritarian regimes such as that in China.
However, Tor is also often criticised for carrying illegal, shady or controversial content such as pornography and “Silk Road” traffic for illegal goods. So an interesting question is what kind of traffic prevails?
Today, we get an answer thanks to the work of Alex Biryukov, Ivan Pustogarov and Ralf-Philipp Weinmann at the University of Luxembourg. And the results are not as eye-sparklingly freedom-protecting as you might imagine.
These guys conclude that the Tor network is dominated by botnet traffic and that much of the rest is adult content and traffic related to black market and illegal goods.
First up, if Tor is so anonymous, how did these guys get their data? It turns out that until recently, the Tor protocol contained a flaw that allowed anybody in the know to track users back to their origin.
This flaw was actually discovered by Biryukov, Pustogarov and Weinmann earlier this year and immediately corrected by Tor. However, before the flaw became public, these guys took the opportunity to analyse Tor traffic to see where it came from and what it contained.
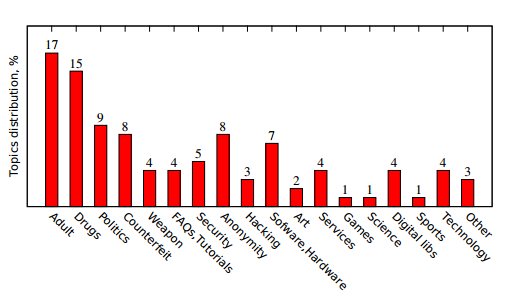
On 4 February, they collected some 39,000 unique addresses offering Tor content. They then estimated the popularity of each address and classified its content. In particular, they roughly divided the addresses into two groups: those providing illegal content or shady services and those providing other hidden services, such as freedom of speech and the anonymous search engine DuckDuckGo.
The results are eye-opening. Biryukov and co say the number of addresses devoted to legal and not-so-legal content is about equal. “Among Tor hidden services one can even find a chess server,” they say.
But a different picture emerges when it comes to the relative popularity of these services. Of the top twenty most popular Tor addresses, eleven are command and control centres for botnets, including all of the top five. Of the rest, five carry adult content, one is for Bitcoin mining and one is the Silk Road marketplace. Two could not be classified.
The FreedomHosting address is only the 27th most popular address while DuckDuckGo is the 157th most popular, according to this analysis.
“The most popular…addresses are command and control centers of botnets and resources serving adult content,” conclude Biryukov and co.
That’s a depressing picture but perhaps it’s the price humanity has to pay for freedom of speech.
Discuss—anonymously or not—in the comments section below.
Ref: arxiv.org/abs/1308.6768: Content And Popularity Analysis Of Tor Hidden Services
Keep Reading
Most Popular
Large language models can do jaw-dropping things. But nobody knows exactly why.
And that's a problem. Figuring it out is one of the biggest scientific puzzles of our time and a crucial step towards controlling more powerful future models.
How scientists traced a mysterious covid case back to six toilets
When wastewater surveillance turns into a hunt for a single infected individual, the ethics get tricky.
The problem with plug-in hybrids? Their drivers.
Plug-in hybrids are often sold as a transition to EVs, but new data from Europe shows we’re still underestimating the emissions they produce.
Google DeepMind’s new generative model makes Super Mario–like games from scratch
Genie learns how to control games by watching hours and hours of video. It could help train next-gen robots too.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.