New Defense Against Denial of Service Attacks: "Bring ’em On!"
A new defense against a Denial of Service attack takes the unconventional route of saying, in essence, “What you got, sucka?” Called Speak-Up, the defense works by asking all clients connecting to a server to beef up the size of their requests.

Most of the time, the theory goes, legitimate clients have way more available bandwidth than attackers, who are probably maxing out their bandwidth while trying to shut you down. As a result, legitimate clients get more of the server’s time–enough, hopefully, to prevent a service interruption.
It’s a little bit like Homer’s punishment for selling his soul in exchange for a donut. Naturally, the devil responds with “Here’s all the donuts in the world!”
In a Distributed Denial of Service attack, miscreants who control large networks of zombie PCs use them to flood a target server–for example, the one hosting this webpage–with so much traffic that it either goes belly up or becomes so congested that no legitimate requests for its attention can get through.
It’s the sort of thing that infamous message board 4chan’s self-described “/b/tards” launched against Gawker.com and, most recently, against the Motion Picture Association of America.
The usual defense against this kind of attack is the most obvious one: try to figure out who are the bad apples sending your server requests, and block them one by one. The problem with this approach is that it takes time to figure out who are the bad guys, and while you’re playing detective, your hosted service or website is effectively inaccessible.
There’s also a risk that any barriers you throw up will block a certain amount of legitimate traffic, which is exactly what the attackers are trying to accomplish in the first place.
Speak-Up turns this notion on its head. Instead of trying to distinguish between legitimate and malicious traffic, it simply asks all clients to send it more and more traffic. From the paper, DDoS Defense by Offense, by Michael Walfish and his colleagues:
When the protected Web server is overloaded, the front-end gives JavaScript to unmodified Web clients that makes them send large HTTP POSTs. These POSTs are the “bandwidth payment.”
This sounds crazy: why would you want a server being crippled by too much traffic to ask for even more traffic? First, know that in Speak-Up, the server isn’t being overloaded–there’s something between it and the internet that is only letting through as many requests as it can handle. Under normal circumstances, the malicious requests would still monopolize the server because they tend to be sent at a much higher rate.
But in Speak Up, a kind of auction occurs: the server is telling all the clients: “Hey, let’s see what you’re made of. Got any more bandwidth for me?” Clients that oblige by, in effect, uploading large-ish files on top of their normal requests, are able to send more traffic, and because the bad guys tend to be bandwidth-limited, this means that the good guys are getting a share of traffic that is at least proportional to their number.
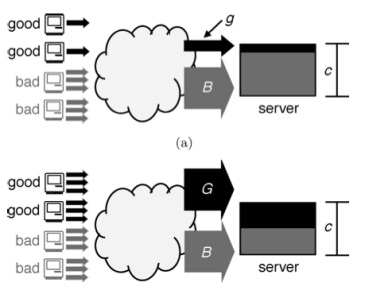
Here’s an illustration of how Speak-Up works: at top, you have the portion of the server’s resources being used by legitimate traffic (black) when the server is under attack and undefended. Bottom, you’ve got the same server with Speak-Up in place. Now, the legitimate traffic is getting its fair share of the server’s resources.
The authors claim that servers defended with Speak-Up don’t have to be as over-provisioned as normal servers, and that as long as the legitimate traffic to a server is within the same order of magnitude as the bad stuff, the legitimate traffic will get through.
There are a host of caveats here. If you want more detail you should read the paper, which is 50 (fairly lucid) pages long before you even get to the references.
Keep Reading
Most Popular
Large language models can do jaw-dropping things. But nobody knows exactly why.
And that's a problem. Figuring it out is one of the biggest scientific puzzles of our time and a crucial step towards controlling more powerful future models.
The problem with plug-in hybrids? Their drivers.
Plug-in hybrids are often sold as a transition to EVs, but new data from Europe shows we’re still underestimating the emissions they produce.
How scientists traced a mysterious covid case back to six toilets
When wastewater surveillance turns into a hunt for a single infected individual, the ethics get tricky.
Google DeepMind’s new generative model makes Super Mario–like games from scratch
Genie learns how to control games by watching hours and hours of video. It could help train next-gen robots too.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.