Flawless Vote Counts
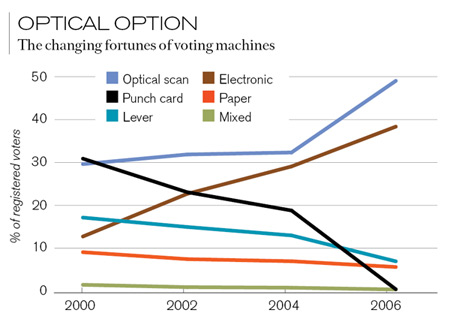
Since the 2000 election debacle, optical scanners have become the most common U.S. voting technology. Voters fill in a bubble next to a candidate’s name on a paper ballot and feed it into the scanner. The scanners tally votes automatically, saving time, but they also leave a paper trail that can be hand audited.
Even optical scanners can misread stray marks, however, and any voting machine can be tampered with after the fact. But a cryptographic system developed under the leadership of electronic-cash pioneer David Chaum can guarantee that every vote cast using an optical scanner is correctly recorded.
In the voting booth, instead of filling in a bubble in pencil, the voter uses a special pen to reveal a code printed inside the bubble in invisible ink. Later, the voter can enter the ballot’s serial number on an election website, which looks up the ballot and displays the associated code. If the code matches the one exposed in the booth, the vote was correctly tallied. But because the codes are never publicly correlated with candidates’ names, the voter’s privacy is maintained–and there’s no evidence to give to would-be vote buyers.
Until now, it’s been easy to dismiss cryptographic voting systems as academic exercises, but the fact that the new system is designed to work with optical scanning gives Chaum hope that it will catch on. “We’re ready,” he says. “There’s no risk. If you add it on, it doesn’t interfere with what you had, and if there’s a problem with it, you can just ignore it.”

Tamper-proof tally: A new cryptographic system can guarantee that votes cast using optical scanners are counted correctly. (1) The voter uses a decoder pen to expose a unique, randomly generated code printed in invisible ink next to a candidate’s name. (2) The voter writes the code on a detachable receipt marked with the ballot’s serial number. (3) An ordinary optical scanner reads the ballot, just as it would one marked in pencil. (4) At home, the voter enters the ballot’s serial number on an election website. If the site pulls up the corresponding code, the vote was recorded accurately.
Credit: Brown Bird Design
Chart source: Election Data Services
Keep Reading
Most Popular
Large language models can do jaw-dropping things. But nobody knows exactly why.
And that's a problem. Figuring it out is one of the biggest scientific puzzles of our time and a crucial step towards controlling more powerful future models.
How scientists traced a mysterious covid case back to six toilets
When wastewater surveillance turns into a hunt for a single infected individual, the ethics get tricky.
The problem with plug-in hybrids? Their drivers.
Plug-in hybrids are often sold as a transition to EVs, but new data from Europe shows we’re still underestimating the emissions they produce.
Google DeepMind’s new generative model makes Super Mario–like games from scratch
Genie learns how to control games by watching hours and hours of video. It could help train next-gen robots too.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.